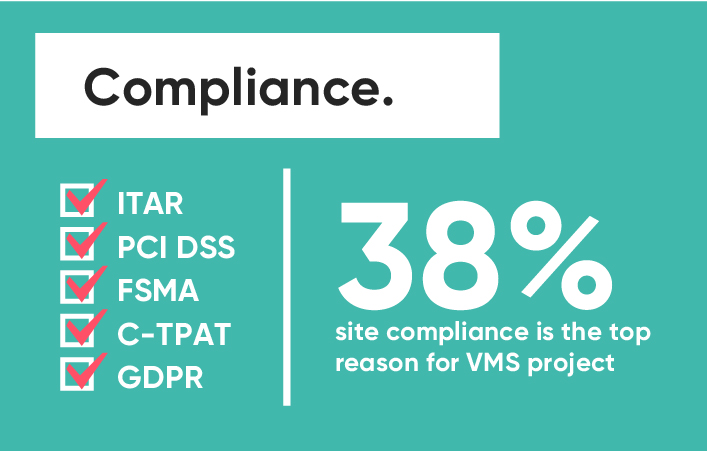
Audits and regulations can have a significant impact on a business. We want to support our customers on their compliance journey and enable them to meet stringent requirements with technology. Working with customers across a wide range of industries, we have been exposed to a variety of regulations. Visitor management is a common foundation. With our customizable platform, organizations can adapt to unique industry or business requirements, as illustrated with this list of common compliance standards.
International Traffic in Arms Regulations
(ITAR)
The International Traffic in Arms Regulations control the export and temporary import of defense articles and services in the United States, affecting any organization involved in the manufacture, sales or distribution. The U.S. government requires manufacturers, exporters, and brokers of defense articles, defense services or related technical data, to be ITAR compliant by law. As ITAR is designed to prevent unauthorized data access by foreign nationals, visitor management is an important component.
How does Sign In Enterprise help you comply?
- Validate a visitor’s identity with ID scanning, photo capture, and pre-registration
- Ensure every visitor is authorized to enter by screening the individual against watch-lists
- Tailor what visitor data is captured, including name, company, purpose of visit and host (employee authorizing access)
- Verify a visitor’s country of origin or citizenship to differentiate between U.S. and other
- Allow U.S. visitor to bypass additional questions during the sign-in process
- Alert security if an unauthorized visitor is attempting to access the facility
- Capture a visitor’s e-signature on NDAs or other legal documents
- Print custom visitor badges for visual identification and access authorization
- Include the country of origin or citizenship on the badge
- Include whether an escort is required or not required
- Insert the name of the host to present the escort responsibility
- Automatically insert an expiration date or use self-expiring badges
- Use adhesive labels to ensure the visitor wears the badge throughout the visit
- Ensure hosts are sent automatic notifications, also outlining their escorting responsibility
- Record a visitor’s history, creating a clear repository of who was on-site at what time
These features also support compliance with the Export Administration Regulations (EAR).
Learn more about ITARPayment Card Industry Data Security Standard
(PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure the safety of cardholder data. Any organization that accepts, processes, stores or transmits credit card information needs to maintain a secure environment, promoting both physical and data security. Part of the PCI Compliance standard is control of physical access to your facility (Section 9). To comply with this requirement, merchants must restrict access to protected areas (ie. your office) and know the difference between customers, staff, and other potential attackers.
How does Sign In Enterprise help you comply?
- Validate a visitor’s identity with ID scanning
- Ensure every visitor is authorized to enter by screening the individual against watch-lists
- Tailor what visitor data is captured, including name, company, purpose of visit and host (employee authorizing access)
- Alert security if an unauthorized visitor is attempting to access the facility
- Capture a visitor’s e-signature on legal documents, such as waivers or NDAs
- Prompt the visitor to watch a compliance video during sign-in, ahead of entering the facility
- Print visitor badges for visual identification and access authorization
- Ensure hosts are sent automatic notifications, also outlining their escorting responsibility
- Record a visitor’s history, creating a clear repository of who was on-site at what time
FDA Food Safety Modernization Act
(FSMA)
Since 2011, organizations operating in the food industry in the United States are required to comply with the Food Safety Modernization Act (FSMA). It is designed to transform the food safety system by regulating how foods are processed and mitigating the risk of intentional contamination. To protect the U.S. food supply, organizations are required to reduce the threats that could impact food production facilities which involves diligent visitor management and controlling who has physical access.
How does Sign In Enterprise help you comply?
- Validate a visitor’s identity with ID scanning
- Ensure every visitor is authorized to enter by screening the individual against watch-lists
- Alert security if an unauthorized visitor is attempting to access the facility
- Capture a visitor’s e-signature on legal documents, such as waivers or NDAs
- Prompt the visitor to watch a compliance video during sign-in, ahead of entering the facility
- Print visitor badges for visual identification and access authorization
- Ensure hosts are sent automatic notifications, also outlining their escorting responsibility
- Record a visitor’s history, creating a clear repository of who was on-site at what time
Customs-Trade Partnership Against Terrorism
(C-TPAT)
The Customs-Trade Partnership Against Terrorism (C-TPAT) is a supply chain security program led by U.S. Customs and Border Protection focused on improving the security of companies’ supply chains with respect to terrorism. The compliance audit is a voluntary government-business initiative to strengthen the cooperation with international supply chain owners such as importers, carriers, consolidators, licensed customs brokers, and manufacturers. To be compliant, organizations need to ensure the integrity of their security practices and mitigate risk by implementing security measures specific to the business nature. The C-TPAT requires control over who has access to a company’s facilities and clear procedures for visitor management.
How does Sign In Enterprise help you comply?
- Validate a visitor’s identity with ID scanning
- Ensure every visitor is authorized to enter by screening the individual against watch-lists
- Alert security if an unauthorized visitor is attempting to access the facility
- Capture a visitor’s e-signature on legal documents, such as waivers or NDAs
- Print visitor badges for visual identification and access authorization
- Ensure hosts are sent automatic notifications, also outlining their escorting responsibility
- Record a visitor’s history, creating a clear repository of who was on-site at what time
Data Residency
Legal or regulatory requirements are imposed on organizations that handle sensitive personal information. Depending on the country or industry such as governmental institutions, medical industries, or education, some organizations are required to store their visitor data locally.
How does Sign In Enterprise help you comply?
To support our international customers, Sign In Enterprise offers the choice between a U.S., EU or Canadian data center. We are committed to data protection and are working on growing the list of data centers to provide the flexibility you need.
General Data Protection Regulation
(GDPR)
The EU General Data Protection Regulation (GDPR) is a new comprehensive data law that is designed to protect and empower all EU citizens data privacy and reshape the way organizations across the region approach data security. It requires companies and governments to be transparent about the personal data they process, have a legitimate purpose for their use of that data, and exercise care in handling data. The GDPR replaces the Data Protection Directive 95/46/EC and is intended to update and harmonize data privacy laws across Europe, with an effective date of May 25, 2018.
The GDPR defines “personal data” as any information related to a natural person (‘Data Subject’), that can be used to directly or indirectly identify the person. It can be anything from a name, a photo, an email address, or a computer IP address. The new regulation significantly expands the privacy rights granted to individuals and places many new obligations on organizations that process personal information.
Organizations can collect personal data only for specified, explicit, and legitimate purposes. To do so, they need to have the data subject’s consent to process personal data. The consent needs to be clear, specific, freely given, and can be revoked at any point in time. It is the organization’s responsibility to be able to prove that they have obtained valid consent and when given, it only relates to the specific relationship.
With the GDPR all EU citizens hold the following data privacy rights:
- Data access: the controller must provide the data subject with information, including the specific data processed, the purposes of the processing, and the other parties with whom such data has been shared
- Data correction: the data subject can request the data to be modified if incomplete or inaccurate
- Restriction of processing: the individual can limit the processing to a specific purpose or party
- Data portability: the person has the right to request a copy of their personal data from the controller
- Right to be forgotten: the data subject can revoke consent and request for data to be erased
- Right to object: the individual can deny data processing, especially if the purpose is related to marketing
Does the GDPR apply to your organization?
The new regulation reaches beyond physical borders and applies to all companies processing and holding the personal data of data subjects residing in the European Union, regardless of the company’s location.
How will Sign In Enterprise help you comply?
The GDPR rules out the paper log book. To be able to protect and manage personal data effectively, organizations are required to shift to a more sophisticated solution. Sign In Enterprise offers a secure and customizable platform and data processing framework to support customers with establishing controls and procedures in data management. With a cloud-based visitor management platform, organizations have more control and can establish procedures to comply with the new regulation.
- Transparency and consent: clearly communicate to the visitor what and why data is captured. Add notifications during the sign-in process and customize the confirmation emails.
- Data collection: comply with data minimization and control what personal data is collected by customizing the sign-in flow. Determine mandatory fields, capture consent, or skip questions for a specific type of visitor.
- Data processing: Prevent unauthorized access to data with customizable user roles. Increase control over who can view, modify, export, or delete personal data within an organization.
- Data requests and transfers: Support an individual’s rights to access and portability with the consolidated repository. Use the search functionality in the digital log book to access and export data for transfers, if requested.
- Data deletion: If requested, visitor data can be deleted to support a data subject’s “right to be forgotten”. Store data only for as long as it is needed to fulfill the original purpose.
- Incident response: Leverage the consolidated view and respond quickly in case of an incident or data breach. Affected data subjects can be immediately notified.
- Data residency: Choose to store visitor data in one of Sign In Enterprise’s local data centers to meet mandates of storing and processing data in a certain country or region.
For more information about the GDPR and data protection, please contact [email protected].
* Sign In Enterprise supports customers in meeting compliance requirements. The management and configuration of the platform is at the discretion of our customers. It is the responsibility of each customer to be compliant with any laws, rules, regulations and standards.